CSE Ph.D. and Faculty Presence at USENIX Security Symposium 2017
The 26th USENIX Security Symposium took place Aug. 16-18 in Vancouver, Canada, and security researchers in the CSE department were well represented on the conference program. Ph.D. students Craig Disselkoen, David Kohlbrenner, Zhaomo Yang and Brian Johannesmeyer had papers on the program, together with CSE faculty including Leo Porter, Dean Tullsen, Hovav Shacham, Sorin Lerner and research scientist Kirill Levchenko.
The three CSE papers on the program and abstracts for each are included below (with links to full papers):
Prime+Abort: A Timer-Free High-Precision L3 Cache Attack Using Intel TSX, by Craig Disselkoen, David Kohlbrenner, Leo Porter, and Dean Tullsen.
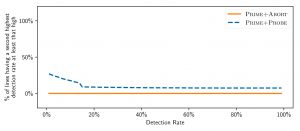
Last-Level Cache (LLC) attacks typically exploit timing side channels in hardware, and thus rely heavily on timers for their operation. Many proposed defenses against such side-channel attacks capitalize on this reliance. This paper presents PRIME+ABORT, a new cache attack which bypasses these defenses by not depending on timers for its function. Instead of a timing side channel, PRIME+ABORT leverages the Intel TSX hardware widely available in both server- and consumer-grade processors. This work shows that PRIME+ABORT is not only invulnerable to important classes of defenses, it also outperforms state-of-the-art LLC PRIME+PROBE attacks in both accuracy and efficiency, having a maximum detection speed (in events per second) 3× higher than LLC PRIME+PROBE on Intel’s Skylake architecture while producing fewer false positives.
On the Effectiveness of Mitigations against Floating-Point Timing Channels, by David Kohlbrenner and Hovav Shacham.
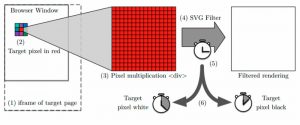
The duration of floating-point instructions is a known timing side channel that has been used to break Same-Origin Policy (SOP) privacy on Mozilla Firefox and the Fuzz differentially private database. Several defenses have been proposed to mitigate these attacks. We present detailed benchmarking of floating-point performance for various operations based on operand values. We identify families of values that induce slow and fast paths beyond the classes (normal, subnormal, etc.) considered in previous work, and note that different processors exhibit different timing behavior. We evaluate the efficacy of the defenses deployed (or not) in Web browsers to floating-point side channel attacks on SVG filters. We find that Google Chrome, Mozilla Firefox, and Apple’s Safari have insufficiently addressed the floating-point side channel, and we present attacks for each that extract pixel data cross-origin on most platforms. We evaluate the vector-operation based defensive mechanism proposed at USENIX Security 2016 by Rane, Lin and Tiwari and find that it only reduces, it does not eliminate, the floating-point side channel signal. Together, these measurements and attacks cause us to conclude that floating point is simply too variable to use in a timing security-sensitive context.
Dead Store Elimination (Still) Considered Harmful, by Zhaomo Yang, Brian Johannesmeyer, Sorin Lerner and Kirill Levchenko (and Aalborg University’s Anders Trier Olesen).
Dead store elimination is a widely used compiler optimization that reduces code size and improves performance. However, it can also remove seemingly useless memory writes that the programmer intended to clear sensitive data after its last use. Security-savvy developers have long been aware of this phenomenon and have devised ways to prevent the compiler from eliminating these data scrubbing operations.
In this paper, we survey the set of techniques found in the wild that are intended to prevent data-scrubbing operations from being removed during dead store elimination. We evaluated the effectiveness and availability of each technique and found that some fail to protect data-scrubbing writes. We also examined eleven open source security projects to determine whether their specific memory scrubbing function was effective and whether it was used consistently. We found four of the eleven projects using flawed scrubbing techniques that may fail to scrub sensitive data and an additional four projects not using their scrubbing function consistently. We address the problem of dead store elimination removing scrubbing operations with a compiler-based approach by adding a new option to an LLVM-based compiler that retains scrubbing operations. We also synthesized existing techniques to develop a best-of-breed scrubbing function and are making it available to developers.
CSE professor Deian Stefan was also at USENIX Security. He chaired a session on “Side-Channel Countermeasures” on the first day of the conference.
