Stefan Savage Addresses Auto Security Vulnerabilities at USENIX Enigma Conference
CNS Co-Director Stefan Savage is on the steering committee of USENIX Enigma, a new, three-day security conference geared towards those working in both industry and research. The inaugural conference took place this week at the Hyatt Regency San Francisco, and Savage made headlines with his Jan. 26 talk on “Modern Automotive Vulnerabilities: Causes, Disclosures and Outcomes.”
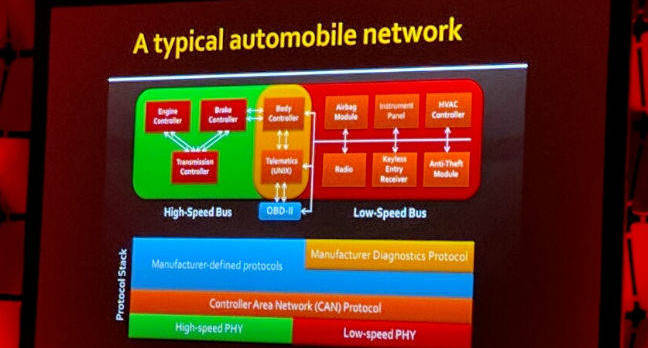
In his presentation on Tuesday, Savage caught the attention of attendees when he noted that his team of researchers were able to control a vehicle by playing a song with malicious code encoded in one of the tracks. “Basically, give me 18 seconds of playtime and we can insert the attack code,” Savage told a reporter from the UK publication The Register.
Savage said that specific flaw has since been addressed, but automobiles remain vulnerable because automakers use a government-mandated OBD-II port, which opens up the car’s network. “For cars, the original equipment manufacturer is not the developer, they are the integrator, so there are software supply chain issues,” he said. “Source code is frequently not available, so code inspection does not work, since no party in the world has access to all of a car’s source code.
The Register quoted Savage as saying that the industry must “adopt automatic wireless software updates to fix problems as they are discovered.” Predicted Savage: “Every manufacturer now either has remote update or will shortly announce it. The cost of not having it is just too great.”
The only other speaker in the session on security in autos was CSE alumnus Tadayoshi Kohno (Ph.D. ’06). Savage sat on Kohno’s Ph.D. dissertation committee with two other CSE faculty, Mihir Bellare and Daniele Micciancio. Today, Kohno is a professor of computer science and engineering at the University of Washington. Kohno’s talk focused on “Computer Security and the Internet of Things.”
A former postdoctoral researcher in CSE’s Security group from 2009 to 2011, Damon McCoy also spoke at USENIX Enigma. His topic: “Bullet-Proof Credit Card Processing.” McCoy is now a professor of computer science and engineering at New York University, where his primary research focus is on online payment systems, the economics of cybercrime. automotive systems, privacy-enhancing technologies and “censorship resistance.”
